From the various news published on the net we have seen how different Instagram profiles belonging to famous people were victim of hacker attacks. Even if this phenomenon affects the VIPs more, however we have decided to make an article in which we list a series of indications for hack or steal Instagram in order to get to know the tricks used by the bad guys. Of course, we will also list several tips to defend you. Let's not waste any more time and find out immediately how to do it.
Before we started, we wanted to clarify that the guide was created for informational purposes only. The content of this article, in fact, does not in any way want to encourage the account theft of the popular social network. Therefore, neither I nor the entire staff of ChimeraRevo we assume responsibility for the use you will make of it.
Content index
- Hack or steal Instagram using passwords saved in the browser
- Hacking or stealing Instagram via phishing
- Hack or steal Instagram with spy apps
- Hack or steal Instagram with keylogger
- Hacking or stealing Instagram: how to defend yourself
Hack or steal Instagram using passwords saved in the browser
One of the techniques of hacking more adopted by attackers to access Instagram profiles is to use a feature found in Web browser most common which allows you to save login passwords in an internal database. Indeed, Chrome, Firefox, Safari, Microsoft Edge and the most popular Internet browsing software allow you to save your login credentials (username or e-mail addresses and passwords) of various web portals without typing them manually each time during the login phase.
While this is a really handy feature, a cyber criminal he can get hold of this information by simply logging into your computer. There is even software, obviously created for legitimate purposes, which can be used by hackers for recover and find in the blink of an eye all Instagram passwords. We are talking about SterJo Instagram Password Finder. The software is only available for Windows and even can be downloaded in portable version, so it leaves no trace as it does not install.
Hacking or stealing Instagram via phishing
Il Phishing it is a particularly widespread technique nowadays which in some cases is very effective. In simple terms, you receive bogus emails from bogus public entities, telephone operators and other entities containing links that refer to scam web pages which require you to enter your account login credentials.
In some cases, these pages are very similar to the original ones, then it's really easy to fall into the trap. Tuttavia, it is possible to escape phishing simply ignoring fake emails and do not click on the link inside them.
Hack or steal Instagram with spy apps
On smartphones and tablets it is possible to easily install spy apps that allow keep track of the activities carried out by the user on their device. Thanks to these software it is possible to see the pages visited on the Internet, the calls received and made, the applications used and even the text typed on the keyboard. All this information comes recovered and sent to hackers using external servers.
Among the most used spy apps are those for the parental control like Qustodio (Android / iOS) and Norton Family Parental Control (Android / iOS). On Android you can also use anti-theft app which are used to find the smartphone in case of theft or loss. One of the most used is Cerberus. In this case, we suggest you read our guide to protect yourself from spying with Cerberus.
Hack or steal Instagram with keylogger
It flies, i cyber criminals they often use i keylogger. Let's talk about applications capable of keep track of activities carried out by a user on a smartphone or PC. For example, i keylogger allow you to monitor the keys typed on the device, then it's easy to get your password out to access Instagram. Among the most popular applications, we have KidLogger, iKeyMonitor and iKeyGuard.
Hacking or stealing Instagram: how to defend yourself
After seeing in general the methods most used by attackers to hack or steal an account of the popular photographic social network, in the following lines we will list the suggestions that you can follow to be more relaxed.
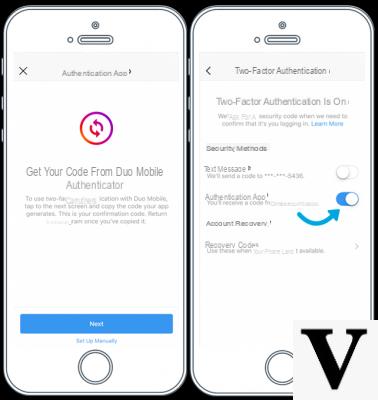
- Enable two-factor authentication from the Settings of Instagram in order to insert a security code received via SMS.
- Set a secure unlock method and complex on your smartphone and / or tablet (face scan, iris recognition, PIN, pattern or fingerprint).
- Your Android, scan installed applications using antivirus or antimalware. In this case, we advise you to read our guide dedicated to the best antivirus for Android.
- Remove any root or jailbreak as spy apps require special permissions in order to function given only by these two things.
- Change your Instagram account password often and above all, do not use an identical one from another social network or account in general.
- Set a long password at least 15 characters containing letters, symbols and numbers.
- Don't lend your smartphone to people you don't know.
- Check the applications installed on the device from the Settings (for example, parental control apps are easily detectable).
- Pay special attention to how much you buy one smartphone used.
- In extremis, make a restore to factory conditions (if you don't know how to do it, read our dedicated guides on how to reset iPhone and Android reset).
Other useful articles
In the list below you will find some posts published on ChimeraRevo which also concern the popular photographic social network now owned by Facebook: